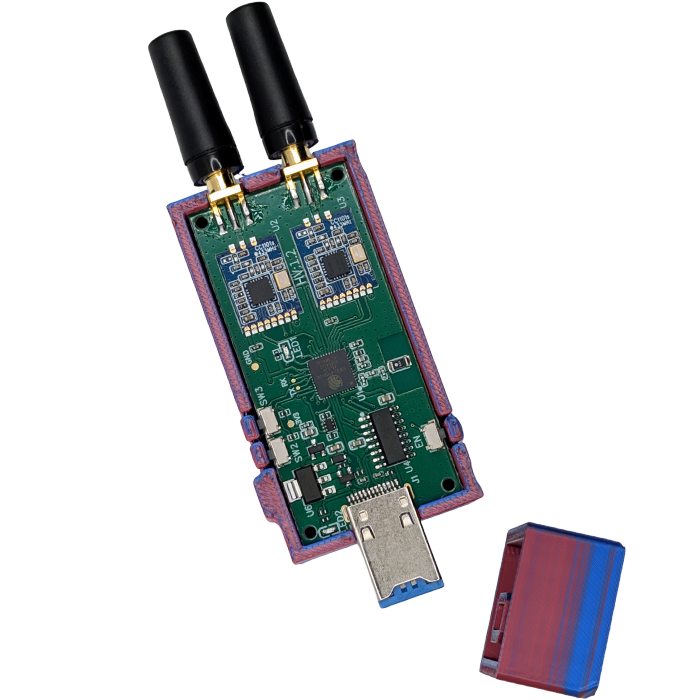
Evil Crow RF V2: Ghost Shell Edition – FREE 3D Printed Case + 32gb SD Card
Unleash the architects of chaos. The Evil Crow RF V2 with the custom “Ghost Shell” 3D-printed case is not just another radio toolkit—it’s the signature weapon of digital mercenaries and cyber-saboteurs who refuse to blend in. Blending open-source rebellion with brutalist cyberpunk design, this is the RF playground built for disruption.
Break out of the corporate sandbox: Evil Crow RF V2 arms you with dual full-duplex transceivers, seamless multi-band support (300–928MHz), and the arsenal to dominate in wireless protocol analysis, signal jamming, and pentesting missions. This beast is encased in a bespoke, high-durability 3D printed shell engineered for urban operations—sleek, menacing, and unapologetically unconventional.
Every curve and angle of the Ghost Shell broadcasts intent: you’re here to pull back the curtain on wireless networks and expose their secrets. No more plastic clones. No more corporate shackles. The Hexmod ethos lives in every detail. Hack, analyze, disrupt—leave your signature on the spectrum.
Forge your legend. Hack the airwaves. This is your RF battlefield.

Hardware and Capabilities
- •RF Chipset & Bands:
- Dual CC1101 modules (Texas Instruments) for sub-GHz mischief and an NRF24L01 for 2.4GHz, all orchestrated by a WiFi-capable ESP32 processor.
- •Frequency Bands:
- •300–348MHz
- •387–464MHz
- •779–928MHz
- •2.4GHz (via NRF24L01)
Simultaneous TX/RX:
Core Functions
Signal Reception & Analysis
- •Capture ambient RF traffic, sniffing everything from keyfobs to weather stations, restaurant buzzers, and home IoT devices.
- •Flexible modulation support—common options include ASK/OOK, FSK, and more, with custom configuration possible.
- Signal Transmission & Replay Attacks
- •Transmit arbitrary signals or previously recorded ones, spoofing legitimate devices for penetration scenarios.
- •Replay is the bread and butter: capture a remote signal, like a garage opener or gate, then retransmit to open said device.
- Brute Force & Jamming
- •Brute force: blast code sequences at a target (within legal boundaries) to find undocumented or weak keys.
- •Jamming: actively interfere with wireless signals, opening up possibilities for denial-of-service testing or signal capture during disruption.
Advanced Red Team Capabalities
- •URH Parse: Export and parse signals for software like Universal Radio Hacker.
- •Mousejacking: Exploit wireless mouse/keyboard vulnerabilities.
- •Rolljam/Rollback: Counter rolling code systems for modern cars and devices.
- •Kaiju Compatibility: Integrate with Kaiju, an online rolling code analyzer, for the most advanced attacks on automotive devices.
Customization & Community
- •Open-source firmware and hardware. Anyone can hack, fork, and improve.
- •Alternative firmwares enhance usability, with new web interfaces, mobile support, and extended attack modes readily available.
- •Buttons are assignable for quick on-the-field attacks or captures—perfect for solo ops or demo scenarios.
User Experience and Workflow
- •Configuration via Web Panel:
- Evil Crow RF V2 runs a WiFi AP—connect any phone or laptop, then configure via your browser (no desktop software needed).
- •OTA Updates & Firmware Hacking:
- The community churns out updates, custom firmwares, and mods—updating and customizing is as simple as flashing a file or visiting a web interface.
- •Automation & Scripting:
- Advanced users can script attacks, automate brute force, or use with signal analysis software thanks to the device’s open architecture.
Real-World Scenarios
- •Red Team on a Mission:
- Scout and clone office badge signals, block garage openers, capture keyfob codes in a parking lot—then slip away before anyone detects a thing.
- •Hardware Security Research:
- Audit IoT devices, reverse engineer proprietary 433MHz gear, and replicate signals for testing defenses.
- •Training & Education:
- Create hands-on wireless hacking labs—no VM or SDR bloat required—just fire up your Evil Crow, capture, transmit, own the air.